Network Addressing
IP addresses are broken into 4 octets (IPv4) separated by dots called dotted decimal notation. An octet is a byte consisting of 8 bits. The IPv4 addresses are in the following form:
192.168.10.1
There are two parts of an IP address:
- Network ID
- Host ID
The various classes of networks specify additional or fewer octets to designate the network ID versus the host ID.
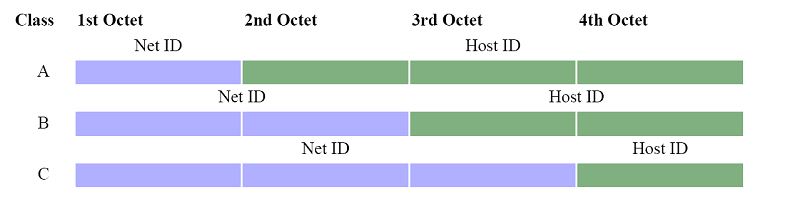
When a network is set up, a netmask is also specified. The netmask determines the class of the network as shown below, except for CIDR. When the netmask is setup, it specifies some number of most significant bits with a 1’s value and the rest have values of 0. The most significant part of the netmask with bits set to 1’s specifies the network address, and the lower part of the address will specify the host address. When setting addresses on a network, remember there can be no host address of 0 (no host address bits set), and there can be no host address with all bits set.
Class A-E networks
The addressing scheme for class A through E networks is shown below. Note: We use the ‘x’ character here to denote don’t care situations which includes all possible numbers at the location. It is many times used to denote networks.
Network Type Address Range Normal Netmask Comments

RFCs 1518 and 1519 define a system called Classless Inter-Domain Routing (CIDR) which is used to allocate IP addresses more efficiently. This may be used with subnet masks to establish networks rather than the class system shown above. A class C subnet may be 8 bits but using CIDR, it may be 12 bits. There are some network addresses reserved for private use by the Internet Assigned Numbers Authority (IANA) which can be hidden behind a computer which uses IP masquerading to connect the private network to the internet. There are three sets of addresses reserved. These address are shown below:
- 10.x.x.x
- 172.16.x.x – 172.31.x.x
- 192.168.x.x
Other reserved or commonly used addresses:
- 127.0.0.1 – The loopback interface address. All 127.x.x.x addresses are used by the loopback interface which copies data from the transmit buffer to the receive buffer of the NIC when used.
- 0.0.0.0 – This is reserved for hosts that don’t know their address and use BOOTP or DHCP protocols to determine their addresses.
- 255 – The value of 255 is never used as an address for any part of the IP address. It is reserved for
broadcast addressing. Please remember, this is exclusive of CIDR. When using CIDR, all bits of the address can never be all ones.
To further illustrate, a few examples of valid and invalid addresses are listed below:
1. Valid addresses:
· 10.1.0.1 through 10.1.0.254
· 10.0.0.1 through 10.0.0.254
· 10.0.1.1 through 10.0.1.254
2. Invalid addresses:
· 10.1.0.0 – Host IP can’t be 0.
· 10.1.0.255 – Host IP can’t be 255.
· 10.123.255.4 – No network or subnet can have a value of 255.
· 0.12.16.89 – No Class A network can have an address of 0.
· 255.9.56.45 – No network address can be 255.
· 10.34.255.1 – No network address can be 255.
Network/Netmask specification
Sometimes you may see a network interface card (NIC) IP address specified in the following manner:
192.168.1.1/24
The first part indicates the IP address of the NIC which is “192.168.1.1” in this case. The second part “/24” indicates the netmask value meaning in this case that the first 24 bits of the netmask are set. This makes the netmask value 255.255.255.0. If the last part of the line above were “/16”, the netmask would
be 255.255.0.0.
Subnet masks
Subnetting is the process of breaking down a main class A, B, or C network into subnets for routing purposes. A subnet mask is the same basic thing as a netmask with the only real difference being that you are breaking a larger organizational network into smaller parts, and each smaller section will use a different set of address numbers. This will allow network packets to be routed between subnetworks. When doing subnetting, the number of bits in the subnet mask determine the number of available subnets. Two to the power of the number of bits minus two is the number of available subnets. When setting up subnets the following must be determined:
- Number of segments
- Hosts per segment
Subnetting provides the following advantages:
- Network traffic isolation – There is less network traffic on each subnet.
- Simplified Administration – Networks may be managed independently.
- Improved security – Subnets can isolate internal networks so they are not visible from external networks.
A 14 bit subnet mask on a class B network only allows 2 node addresses for WAN links. A routing algorithm like OSPF or EIGRP must be used for this approach. These protocols allow the variable length subnet masks (VLSM). RIP and IGRP don’t support this. Subnet mask information must be transmitted on the update packets for dynamic routing protocols for this to work. The router subnet mask is different than the WAN interface subnet mask.
One network ID is required by each of:
- Subnet
- WAN connection
One host ID is required by each of:
- Each NIC on each host.
- Each router interface.
Types of subnet masks:
- Default – Fits into a Class A, B, or C network category
- Custom – Used to break a default network such as a Class A, B, or C network into subnets.
IPv6
IPv6 is 128 bits. It has eight octet pairs, each with 16 bits and written in hexadecimal as follows:
2b63:1478:1ac5:37ef:4e8c:75df:14cd:93f2
Extension headers can be added to IPv6 for new features.
Supernetting
Supernetting is used to help make up for some of the shortage if IP addresses for the internet. It uses Classless Inter-Domain Routing (CIDR). If a business needs a specific number of IP addresses such as 1500, rather than allocating a class B set of addresses with the subnet mask of 255.255.0.0, a subnet mask of 255.255.248.0 may be allocated. Therefore the equivalent of eight class C addresses have been allocated. With supernetting, the value of 2 is not subtracted from the possible number of subnets since the router knows that these are contiguous networks. 8 times 254 = 2032.
What section of this document to read next
At this point the reader should have enough fundamental knowledge to grasp routing, so the reader may continue on or skip to the section entitled, “simple routing”. The reader may at this time read all the sections in the “Functions” group of sections, then continue back at the section after this one where you left off.
