Firewalls
Firewalls are mainly used as a means to protect an organization’s internal network from those on the outside (internet). It is used to keep outsiders from gaining information to secrets or from doing damage to internal computer systems. Firewalls are also used to limit the access of individuals on the internal network to services on the internet along with keeping track of what is done through the firewall. Please note the difference between firewalls and routers as described in the second paragraph in the IP Masquerading section.
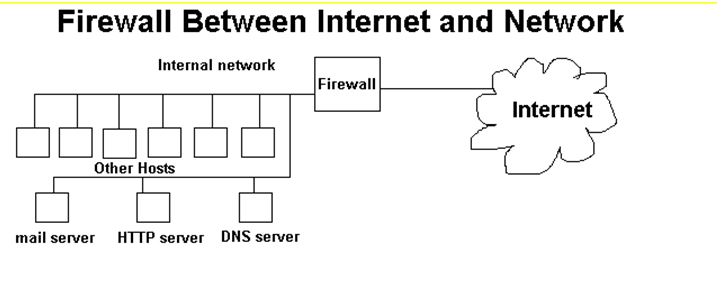
Types of Firewalls
1. Packet Filtering – Blocks selected network packets.
2. Circuit Level Relay – SOCKS is an example of this type of firewall. This type of proxy is not aware of applications but just cross links your connects to another outside connection. It can log activity, but not as detailed as an application proxy. It only works with TCP connections, and doesn’t provide for user authentication.
3. Application Proxy Gateway – The users connect to the outside using the proxy. The proxy gets the information and returns it to the user. The proxy can record everything that is done. This type of proxy may require a user login to use it. Rules may be set to allow some functions of an application to be done and other functions denied. The “get” function may be allowed in the FTP application, but the “put” function may not.
Proxy Servers can be used to perform the following functions.
- Control outbound connections and data.
- Monitor outbound connections and data.
- Cache requested data which can increase system bandwidth performance and decrease the time it takes for other users to read the same data.
Application proxy servers can perform the following additional functions:
- Provide for user authentication.
- Allow and deny application specific functions.
- Apply stronger authentication mechanisms to some applications.
Packet Filtering Firewalls
In a packet filtering firewall, data is forwarded based on a set of firewall rules. This firewall works at the network level. Packets are filtered by type, source address, destination address, and port information. These rules are similar to the routing rules explained in an earlier section and may be thought of as a set of instructions similar to a case statement or if statement. This type of firewall is fast, but cannot allow access to a particular user since there is no way to identify the user except by using the IP address of the user’s computer, which may be an unreliable method. Also the user does not need to configure any software to use a packet filtering firewall such as setting a web browser to use a proxy for access to the web. The user may be unaware of the firewall. This means the firewall is transparent to the client.
Circuit Level Relay Firewall
A circuit level relay firewall is also transparent to the client. It listens on a port such as port 80 for http requests and redirect the request to a proxy server running on the machine. Basically, the redirect function is set up using ipchains then the proxy will filter the package at the port that received the redirect.
Configuring a Proxy Server
The following packages are available in Linux:
- Ipchains soon to be replaced by netfilter (Packet filtering supported by the Linux kernel). It comes with Linux and is used to modify the kernel packet routing tables.
- SOCKS – Circuit Switching firewall. Normally doesn’t come with Linux, but is free.
- Squid – A circuit switching proxy. Normally comes with Linux.
- Juniper Firewall Toolkit – A firewall toolkit product used to build a firewall. It uses transparent filtering, and is circuit switching. It is available as open source.
- The TIS Firewall Toolkit (FWTK). A toolkit that comes with application level proxies. The applications include Telnet, Rlogin, SMTP mail, FTP, http, and X windows. it can also perform as a transparent proxy for other services.
